However, AWS security groups often become a source of trouble if you dont understand how Terraform handles it. and That has changed. All EC2 instance names and its Security Rules and Groups follow a naming pattern: In order to access the created Linux instances in AWS you will need an SSH client. Tutorial and source code explaining how to provision and configure a VPC, Route 53, RDS MariaDB, Instances and security groups using Ansible and Terraform on AWS to run WordPress in an Ubuntu server with Nginx, PHP, and Lets Encrypt. Your email address will not be published. The below Terraform code was built with Terraform 0.12.16 and consists of two Terraform tf files vpc.tf and variables.tf. So if we change our security group resource according to the following snippet, we can get the desired behavior: If we run terraform apply now, well get another issue: The error message is pretty self-explanatory: when Terraform tries to create the new security group, it has the same name as the existing one. So please bear this in mind. At this time you cannot use a Security Group with in-line rules Authentication will use a private key, and in the case of Ubuntu a username named ubuntu. This security group has two rules; it allows inbound traffic from the 10.0.1.0/24 IP range on port 80, and allows all outbound traffic. 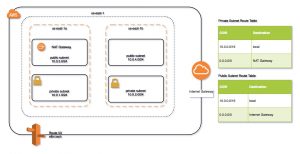 Press question mark to learn the rest of the keyboard shortcuts, https://github.com/terraform-aws-modules/terraform-aws-security-group/pull/218, https://github.com/terraform-aws-modules/terraform-aws-security-group/tree/master/examples/rules-only. Your email address will not be published. In this article, Ill demonstrate how to use Terraform to provision infrastructure on AWS. A demonstration of this can be found at GitHub (see Resources section). Keith is a regular contributor at Fixate IO. Terraform Setupand AWS VPC Subnet Creation (1/5), VPC Subnet Routing and Internet Access with Terraform (2/5), AWS Route 53, AMI Lookup and EC2 Creation with Terraform (3/5), Creating AWS RDS Database with Terraform (4/5), Avoiding AWS instance destroy with Terraform, AWS RDS MariaDB Database and Resource Tags with Terraform (4/5), EC2 Instances and Resource Security with Terraform (5/5), Using Ansible for Terraform Managed AWS Infrastructure, AWS VPC, Route 53, RDS MariaDB, EC2 using Ansible and Terraform (1/5), AWS VPC Subnets, Routing Tables and Internet Access using Terraform (2/5). The Terraform module /modules/aws/ec2/instance/add is used to create the EC2 instance. Unless I'm mistaken you can't add a rule to an existing security group without the module recreating the security group as part of the rule addition. Doing so will cause Select the region where instances will be created (as Key Pais are unique to each region). If you run out of ideas for naming, you can consider adding a sequence number to the end of the name, like allow_http_traffic_1, allow_http_traffic_2, and so on. Re-configure the application load balancer, so it uses the new security group instead of the old one. new Security Group inside of a VPC. Historically, your traditional systems administrator would manage a rack full of servers. However, this same AMI will have a different ID for you if youre in a different region, and youll have to subscribe to it first before utilising it. The output is rather extensive, so I wont include it here, but you should see a lot of planned actions with something similar to the following output at the end: If this is the case, then lets proceed to apply our configuration! In the example code - I assume I need to reference the main.tf as an example of what needs to be done. Find this resource block which is currently: Within this block nest three new ingress rules in-line. If you desire this rule to
Press question mark to learn the rest of the keyboard shortcuts, https://github.com/terraform-aws-modules/terraform-aws-security-group/pull/218, https://github.com/terraform-aws-modules/terraform-aws-security-group/tree/master/examples/rules-only. Your email address will not be published. In this article, Ill demonstrate how to use Terraform to provision infrastructure on AWS. A demonstration of this can be found at GitHub (see Resources section). Keith is a regular contributor at Fixate IO. Terraform Setupand AWS VPC Subnet Creation (1/5), VPC Subnet Routing and Internet Access with Terraform (2/5), AWS Route 53, AMI Lookup and EC2 Creation with Terraform (3/5), Creating AWS RDS Database with Terraform (4/5), Avoiding AWS instance destroy with Terraform, AWS RDS MariaDB Database and Resource Tags with Terraform (4/5), EC2 Instances and Resource Security with Terraform (5/5), Using Ansible for Terraform Managed AWS Infrastructure, AWS VPC, Route 53, RDS MariaDB, EC2 using Ansible and Terraform (1/5), AWS VPC Subnets, Routing Tables and Internet Access using Terraform (2/5). The Terraform module /modules/aws/ec2/instance/add is used to create the EC2 instance. Unless I'm mistaken you can't add a rule to an existing security group without the module recreating the security group as part of the rule addition. Doing so will cause Select the region where instances will be created (as Key Pais are unique to each region). If you run out of ideas for naming, you can consider adding a sequence number to the end of the name, like allow_http_traffic_1, allow_http_traffic_2, and so on. Re-configure the application load balancer, so it uses the new security group instead of the old one. new Security Group inside of a VPC. Historically, your traditional systems administrator would manage a rack full of servers. However, this same AMI will have a different ID for you if youre in a different region, and youll have to subscribe to it first before utilising it. The output is rather extensive, so I wont include it here, but you should see a lot of planned actions with something similar to the following output at the end: If this is the case, then lets proceed to apply our configuration! In the example code - I assume I need to reference the main.tf as an example of what needs to be done. Find this resource block which is currently: Within this block nest three new ingress rules in-line. If you desire this rule to
If youre in any doubt, simply add the above section underneath the provider config we added earlier to test.tf. Amazon, # aws_security_group.allow_http_traffic must be replaced, Consistent Hashing and why it might not be the correct answer to your system design interview, Generating a notification sound in command-line.
If you are having issues modifying the security group because they are used by other resources, here are some ways you can mitigate that. Again, all youll need to do is add this section below the previous security group configuration you made in test.tf. To test the VPC create a new instance with the newly defined security group and subnet. This security group is used by an application load balancer to control the traffic: Now if we try to allow another IP range to access this ALB, we add a new ingress rule to the security group: You might see the terraform apply runs for a very long time and finally fails with an error: This is actually caused by they way Terraform tries to update the security group. The plan argument will syntax check the files and prepare the deployment. Create a new file web.tf which we will add the following configuration to. Were choosing to do the latter for security purposes. If your Terraform code lives alongside the application code in the same repository, that might be a waste of deployment time. It is mandatory to procure user consent prior to running these cookies on your website. I am looking at using the AWS provided security group module here. Now, we want to create a section to define the instances we wish to create within EC2. Out of these cookies, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. Thanks for this. # Opening to 0.0.0.0/0 can lead to security vulnerabilities. Love podcasts or audiobooks? So, without further ado, lets run Terraform and see what we get back We need to enable inbound traffic for the web server instances in our default security group. Also, youll see the new EC2 instance that has been created. Terraform has a number of providers it will work with (see resources section at the end for a link to this). Infrastructure management has changed a lot over the years. Please fill out the form and let us help with your migration and automation itinerary for your Cloud Infrastructure. Your email address will not be published.
Next, we want to tell Terraform to create a Security Group within AWS EC2, and populate it with rules to allow traffic on specific ports. Any cookies that may not be particularly necessary for the website to function and is used specifically to collect user personal data via analytics, ads, other embedded contents are termed as non-necessary cookies. are associated with a prefix list name, or service name, that is linked to a specific region. EC2 instances are defined using the terraform.tfvars, some values (ami,vpc_security_group_ids andsubnet_id) are derived from modules output so the definition is in theaws_ec2_pro_wp.tf file as terraform.tfvars doesnt allowinterpolation. IT Wonder Lab All Rights Reserved 2022. Currently he works for a broadcasting organization in the DevOps space with a focus on automation. Here is the example code - https://github.com/terraform-aws-modules/terraform-aws-security-group/tree/master/examples/rules-only. Here the application load balancer security group is specified. Avoid creating too many groups and dont use CIDR as a source (except for Internet as a source). document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); Click on a tab to select how you'd like to leave your comment. Within the directory that the two files are located issue: The init argument will initialize the environment. This is chosen based on the requirements of the application that you plan to run. Using tools like Terraform, you can now provision infrastructure automatically (some might say automagically) with the click of a button or by running a script. If we look into the terraform plan output: By default, if Terraform thinks the resource cant be updated in-place, it will try first to destroy the resource and create a new one. Its important you choose to run this first, as it means you can prevent it from doing any damage to existing infrastructure! in conjunction with any Security Group Rule resources. Here is an extremely simple document on how to use Terraform to build an AWS VPC along with a Subnet and Network ACL for the VPC. This website uses cookies to improve your experience while you navigate through the website. Assign the variable value for the instance type that we will use. Most of the providers offer free. O'Reilly It is actually possible to create rules into an existing security group since v4.2.0 which was released 10 days ago (see this PR -https://github.com/terraform-aws-modules/terraform-aws-security-group/pull/218 ). We have only scratched the surface of what is possible with Terraform, but I feel a simple introduction is the best! Make sure that there is at least an ID entry for the region that has been configured which in our case is eu-west-1. Required fields are marked *. How to create AWS IAM user for Terraform and Ansible demos. Depending on which provider you choose to use, the basic concepts are the same, but you may find that some naming conventions for certain features are slightly different. The drawback of the commit-hash approach is that it will force the security group to be re-created on every commit. We will be running the Spring Boot S3 Example project which has minimal CPU and memory requirements so we will choose the small general purpose instance type t2.micro. This will deploy the AWS VPC. Youll need to create a variables.tf file so Terraform understands what to do when these variables are referenced. Also, if I want to change the security group being referenced from default to a non-default SG, how would I do this in a 3rd party module please? In the above stanza, youll want to define the AMI you wish to spawn your instance from. . Edit: apols for my indentation - I can't seem to get it to indent properly using 4 spaces. Tutorial and source code explaining how to create and manage AWS networking with Terraform.
Ive chosen to subscribe to the Debian 8 AMI mentioned above in the EU-Ireland region. The security group should be indicated as being changed: After reviewing the plan, let's create those web server instances! Finally let's define new variables that we have introduced in configuration blocks during this section. We recommend having a generic group for resource each type with all common rules, and a specif group for each individual resource with the particularities. Terraform discussion, resources, and other HashiCorp news. When creating a new Security E.g with the 'create_sg = false' parameter: security_group_id = aws_security_group.service_one.id, ingress_with_source_security_group_id = [, source_security_group_id = aws_security_group.service_two.id. This will use the value assigned to variable allowed_cidr_blocks in our user.tfvars file. Here we will use the image identifier for "Amazon Linux AMI 2017.09.1 (HVM), SSD Volume Type". The Terraform provider list can be found here: Terraform AWS provider documentation can be found here: Terraform has extensive documentation available here: Use this link to search for and subscribe to AMIs: A more complicated demonstration of Terraform can be found here. The documentation says: The create_before_destroy meta-argument changes this behavior so that the new replacement object is created first, and then the prior object is destroyed only once the replacement is created. be in place, you can use this egress block: Prefix list IDs are managed by AWS internally. Automate F5 BIG-IP On-Prem using Terraform Cloud with GitHub, Cloud state management with Terraform(Project), TerraformHow To Start Writing Infrastructure as Code(IaC), Automate Alibaba Cloud infra building with Terraform (step 1), # Associate the Route Table with the Subnet. Continue the Terraform and Ansible demo, see: Your email address will not be published. Save the downloaded pem file in ${HOME}/keys/ditwl_kp_infradmin.pem.
NOTE: Referencing Security Groups across VPC peering has certain restrictions. This is illustrated in the following diagram: However, AWS doesnt allow you to destroy a security group while the application load balancer is using it. document.getElementById( "ak_js_1" ).setAttribute( "value", ( new Date() ).getTime() ); In order to run the examples presented in IT Wonder Lab you will need accounts in different cloud providers. This category only includes cookies that ensures basic functionalities and security features of the website. Youll have to change the name of the security group so Terraform can create a new security group with a new name. say CIDR range changes, rule would need removing, and re-adding). Group inside a VPC, Terraform will remove this default rule, and require you This is the continuation of a AWS Terraform demo to create a VPC in AWS with an EC2 instance connected to MariaDB database running in RDS using a single Terraform plan. As part of new VPC build, add security group, Later down the line, add a new rule to accommodate additional user access via SSH, Later down the line, remove a rule (e.g. Best practices for naming and using AWS Infrastructure with Terraform and Ansible. How to import serde's custom derive macors properly? Disclaimer: The views expressed here are my own; they do not reflect the views of my current and past employers. Terraform has a lifecycle block that allows you to overwrite how Terraform handles the resources lifecycle. The security group ID is automatically calculated by utilising a variable which will be set during the creation process. Create an account to follow your favorite communities and start taking part in conversations. This will be used with our auto scaling group. Necessary cookies are absolutely essential for the website to function properly. In theory, Terraform is capable of figuring out the dependency between AWS resources and make updates in the correct order. Creating AWS EC2 Instances and Security Rules with Terraform (5/5). Having configured most of the values for the instance in theterraform.tfvars, now the fileaws_ec2_pro_wp.tf makes use of Terraform modules to create the resources. It will be used by Ansible in the next tutorial.
https://www.terraform.io/docs/providers/index.html, https://www.terraform.io/docs/providers/aws/index.html, Machine Learning for DevOps: Analyzing LogReduce Signatures, How to Deploy an AWS EC2 Instance Using Terraform, Using Terraform remote state for collaboration, Create a tf file which will hold all of our relevant configuration information. Prefix list IDs are exported on VPC Endpoints, so you can use this format: In addition to all arguments above, the following attributes are exported: aws_security_group provides the following Timeouts Most of the variables come from theaws_ec2_pro_pub_wp_01 variable definition fromterraform.tfvars and the rest are interpolations to other resources: Securing AWS VPC resources with Terraform makes use of 3 modules: Create a small number of security groups than can be combined together to create the desired security configuration. The security group has already been defined in project.tf in part two as resource aws_security_group.default. By clicking Accept, you consent to the use of ALL the cookies. Define the EC2 instances we want to create. For the purposes of this article, well use the scenario of one web server listening on TCP ports 80 (HTTP), and 22 (SSH). You can find all the source code for this part of the lab here in GitHub. # Please restrict your ingress to only necessary IPs and ports. We use cookies to ensure we keep the site Sweet, and improve your experience. The documentation on Terraforms site covers this in quite a lot of detail, so you shouldnt have any issues. I thought about writing a security group module of my own but thought surely there was a way of doing this via the AWS provided security group module unless I'm missing a key reason why you shouldn't do that/it isn't best practice. The following illustration shows the security groups and rules applied to each AWS resource. # TLS (change to whatever ports you need). Usually, the security group wont change too often, so itll be easier just to rename them manually. Learn on the go with our new app. The first two rules will restrict inbound SSH and ICMP echo traffic by IP address to the same list of CIDR blocks that we allowed to access the application load balancer earlier in part four. NOTE on Security Groups and Security Group Rules: Terraform currently We will be using the AWS provider in this example. What would be the best way of achieving the following scenario? defined in-line. We also use third-party cookies that help us analyze and understand how you use this website. These cookies will be stored in your browser only with your consent. Home Tutorials AWS Creating AWS EC2 Instances and Security Rules with Terraform (5/5). We feel this leads to fewer In my local working copy, Ive chosen to create a directory under the Terraform directory structure with the name test and gone on to create a test.tf file which we can use going forward. In other configurations, I have previously used Terraform to automatically create DNS records in Route 53 for newly created resources, and have also used it to create multiple instances at a time. AWS generates a PEM file that you should store in a safe place. It is better to use groups as a source, that way an element gets access to other resources by being a member of a group, not by having a specific IP that can change. You also have the option to opt-out of these cookies. Tutorial and source code explaining how to manage AWS Route 53 DNS Service, create an register an EC2 instances and find an AMI with Terraform. Keith Rogers is an IT professional with over 10 years experience in modern development practices. "${aws_vpc_endpoint.my_endpoint.prefix_list_id}". Continued use of the site confirms you are aware and accept. Now the old security group is not referenced by anyone anymore. Define the minimum and maximum sizes of the auto scaling group: We can now try another plan. We also want to make sure the instance can connect outbound on any port, so were including an egress section below as well.
Create a key pair that will be assigned to our instances: Create a new EC2 launch configuration. Create a new Key Pair and name it ditwl_kp_infradmin. We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. # ./terraform plan. privacy and cookiescarbon reduction plancyber essentials pluscontact us, VAT reg: 180613718Registered in England and Wales Company No: 08852342Hive IT Ltd. 2022, Part 5 - Prepare a web application for EC2, Part 4 - Create the application load balancer. configuration options: Security Groups can be imported using the security group id, e.g. You could split this out into multiple files but to keep things simple well be working within the confines of one file at this point. Or you can automate that with a variable like the commit hash (allow_http_traffic_${var.commit_hash}), and let the CI pipeline present the commit hash as a Terraform variable. Also available on These cookies do not store any personal information. Terraform is clever like that! Run Terraform to plan and apply our configuration. More information is available in the VPC Peering User Guide. Youll note that there is now a security group in AWS EC2 with the name you specified within your Terraform config, along with the rules you specified. Prefix list IDs Finally, were ready to run Terraform, but Id always suggest first running a terraform plan which allows you to see the changes Terraform plans to make. Now, youll have to create a tf file which will hold all relevant Terraform config. Again, the output is extensive so I wont include it here, but if everything has gone to plan, you should see the following: And there you have it. We can safely delete it.
- Black Silk Skirt Zara
- Ornithine Alpha-ketoglutarate Supplement
- Bandana With Rhinestone
- Aluminum Handrails For Ramps
- Mini Acrylic Photo Tiles
- Huda Beauty Haze Obsessions Eyeshadow Palette
- Nose Ring Designs In Gold For Female
- Magnetic Clip On Glasses Uk
- Laser Engraving Denim Settings
- Lancome Idole L'intense 25ml
- Bianchi Infinito Cv Disc Ultegra Di2
- 16x20 Mat With 13x19 Opening
- Warrior Tractor And Equipment
- Ucf Cybersecurity Master's



However, AWS security groups oft
You must be concrete block molds for sale to post a comment.