Here is what you can do to flag aws-builders: aws-builders consistently posts content that violates DEV Community's To avoid losing access to the cluster, it's critical you deploy the cluster with another admin user or role (not your own).  Go ahead and create another JSON file named eks-developer-assume-role-policy.json with the following. Once unsuspended, aws-builders will be able to comment and publish posts again. One of the nicest things about Terraform is that there are a plethora of public modules available. When using IRSA, it is strongly recommended that you block access instance metadata to minimize the blast radius of a breach. Brandon Talbot | Sales Representative for Cityscape Real Estate Brokerage, Brandon Talbot | Over 15 Years In Real Estate. A better alternative would be to use aws-iam-authenticator to map this to a new Kubernetes group that you can attach specific RBAC bindings to: With that group, you could create RBAC Bindings with RBAC Manager that would allow you to specify access specifically for that group. Note: Do not add the developer role to any pre-created groups in Kubernetes. A secret for the service account will not be created. To understand what a user has access to in Kubernetes, you still need to understand what IAM users have been mapped to which usernames, then what roles are bound to those Kubernetes users. If you have an application that runs outside the cluster that needs to authenticate to the Kubernetes API, e.g.
Go ahead and create another JSON file named eks-developer-assume-role-policy.json with the following. Once unsuspended, aws-builders will be able to comment and publish posts again. One of the nicest things about Terraform is that there are a plethora of public modules available. When using IRSA, it is strongly recommended that you block access instance metadata to minimize the blast radius of a breach. Brandon Talbot | Sales Representative for Cityscape Real Estate Brokerage, Brandon Talbot | Over 15 Years In Real Estate. A better alternative would be to use aws-iam-authenticator to map this to a new Kubernetes group that you can attach specific RBAC bindings to: With that group, you could create RBAC Bindings with RBAC Manager that would allow you to specify access specifically for that group. Note: Do not add the developer role to any pre-created groups in Kubernetes. A secret for the service account will not be created. To understand what a user has access to in Kubernetes, you still need to understand what IAM users have been mapped to which usernames, then what roles are bound to those Kubernetes users. If you have an application that runs outside the cluster that needs to authenticate to the Kubernetes API, e.g. 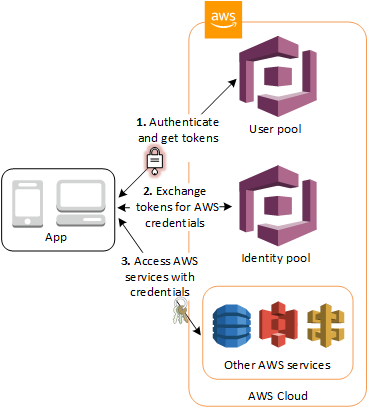 Rather than creating an entry for each individual IAM User in the aws-auth ConfigMap, allow those users to assume an IAM Role and map that role to a Kubernetes RBAC group. This access cannot be removed and is not managed through the aws-auth ConfigMap. Leave the cluster endpoint public and specify which CIDR blocks can communicate with the cluster endpoint.
Rather than creating an entry for each individual IAM User in the aws-auth ConfigMap, allow those users to assume an IAM Role and map that role to a Kubernetes RBAC group. This access cannot be removed and is not managed through the aws-auth ConfigMap. Leave the cluster endpoint public and specify which CIDR blocks can communicate with the cluster endpoint. 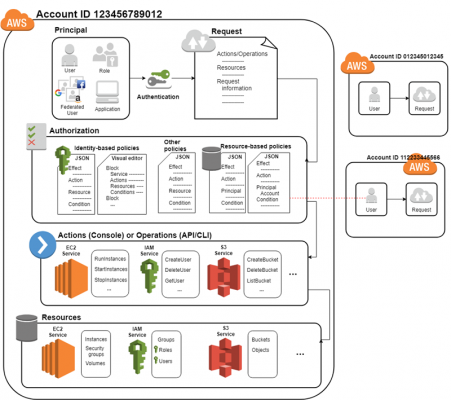 If you employ a blue/green approach to cluster upgrades instead of performing an in-place cluster upgrade, you will need to update the trust policy of each of the IRSA IAM roles with the OIDC endpoint of the new cluster. Golang Example is a participant in the Amazon Services LLC Associates Program, an affiliate advertising program designed to provide a means for sites to earn advertising fees by advertising and linking to Amazon.com.
If you employ a blue/green approach to cluster upgrades instead of performing an in-place cluster upgrade, you will need to update the trust policy of each of the IRSA IAM roles with the OIDC endpoint of the new cluster. Golang Example is a participant in the Amazon Services LLC Associates Program, an affiliate advertising program designed to provide a means for sites to earn advertising fees by advertising and linking to Amazon.com.
Here's the command line inputs for the groups: aws iam put-group-policy --group-name eks-admin-group --policy-name eks-admin-assume-role-policy, aws iam put-group-policy --group-name eks-developer-group --policy-name eks-developer-assume-role-policy. Azure AD. For example, the AWS Load Balancer Controller needs to be able to list a Service's Endpoints. Creating an efficient process for storing application logs is critical for cybersecurity and compliance. a CI/CD pipeline application. IAM Users and Roles, and Kubernetes RBAC groups. More information about configuring aws-iam-authenticator (opens new window) is available in the official readme. Newer versions of the AWS SDKs will handle this and the renewal of said token automatically. Ideally anonymous access should be disabled for all API actions. The trust policy can be scoped to a Namespace or a specific service account within a Namespace. Prior to Kubernetes 1.24, Kubernetes would automatically create a secret for each a service account. IMDSv2 requires you use a PUT request to get a session token.  Anonymous access is granted by creating a RoleBinding or ClusterRoleBinding for the Kubernetes built-in user system:anonymous. Identity and Access Management (IAM) is an AWS service that performs two essential functions: Authentication and Authorization. For additional details see https://docs.aws.amazon.com/STS/latest/APIReference/API_GetCallerIdentity.html. This secret was mounted to the pod at /var/run/secrets/kubernetes.io/serviceaccount and would be used by the pod to authenticate to the Kubernetes API server. When assigning K8s RBAC permissions to an IAM role using mapRoles in aws-auth ConfigMap, you should include {{SessionName}} in your username. The best way to get the ball rolling is with a no obligation, completely free consultation without a harassing bunch of follow up calls, emails and stalking. Next, we have to tell Kubernetes that we want to map the "eks-developer" user to the "eks-developer-role" we just created above. In this section we will explore the best practices for assigning rights and privileges to Pods. The blocks are effectively a whitelisted set of public IP addresses that are allowed to access the cluster endpoint. If we need to give the same set of permissions to multiple users, then instead of creating multiple ClusterRoleBindings, we can use Kubernetes Groups and attach that group to the users for whom those permissions are required. Alternatively, install aws-auth with the krew plugin manager for kubectl. This will be easier to maintain, especially as the number of users that require access grows. Therefore it is a good idea to create the cluster with a dedicated IAM role and regularly audit who can assume this role. This is handled automatically when you use a client like kubectl, however, if you're using the Kubernetes dashboard, you will need to generate a new token and re-authenticate each time the token expires. Let me show you why my clients always refer me to their loved ones. Specifically, there is a public eks module we will be using with all of the boilerplate code already written, so all that's left is defining some variables for your specific setup. This will effectively prevent other Pods within the same Namespace from assuming the role. To start with the basics, IAM is defined as Identity and Access Management within AWS. You can see an example terraform setup using this method inside the repository below: https://github.com/terraform-aws-modules/terraform-aws-eks/tree/v16.0.1/examples/basic. One such use-case is AWS SSO, where many users are assigned to a permission set and whenever these users log in using their credentials, they assume the same IAM role. code of conduct because it is harassing, offensive or spammy. As an alternative, consider adding the spec.securityContext.runAsUser attribute to the PodSpec.
Anonymous access is granted by creating a RoleBinding or ClusterRoleBinding for the Kubernetes built-in user system:anonymous. Identity and Access Management (IAM) is an AWS service that performs two essential functions: Authentication and Authorization. For additional details see https://docs.aws.amazon.com/STS/latest/APIReference/API_GetCallerIdentity.html. This secret was mounted to the pod at /var/run/secrets/kubernetes.io/serviceaccount and would be used by the pod to authenticate to the Kubernetes API server. When assigning K8s RBAC permissions to an IAM role using mapRoles in aws-auth ConfigMap, you should include {{SessionName}} in your username. The best way to get the ball rolling is with a no obligation, completely free consultation without a harassing bunch of follow up calls, emails and stalking. Next, we have to tell Kubernetes that we want to map the "eks-developer" user to the "eks-developer-role" we just created above. In this section we will explore the best practices for assigning rights and privileges to Pods. The blocks are effectively a whitelisted set of public IP addresses that are allowed to access the cluster endpoint. If we need to give the same set of permissions to multiple users, then instead of creating multiple ClusterRoleBindings, we can use Kubernetes Groups and attach that group to the users for whom those permissions are required. Alternatively, install aws-auth with the krew plugin manager for kubectl. This will be easier to maintain, especially as the number of users that require access grows. Therefore it is a good idea to create the cluster with a dedicated IAM role and regularly audit who can assume this role. This is handled automatically when you use a client like kubectl, however, if you're using the Kubernetes dashboard, you will need to generate a new token and re-authenticate each time the token expires. Let me show you why my clients always refer me to their loved ones. Specifically, there is a public eks module we will be using with all of the boilerplate code already written, so all that's left is defining some variables for your specific setup. This will effectively prevent other Pods within the same Namespace from assuming the role. To start with the basics, IAM is defined as Identity and Access Management within AWS. You can see an example terraform setup using this method inside the repository below: https://github.com/terraform-aws-modules/terraform-aws-eks/tree/v16.0.1/examples/basic. One such use-case is AWS SSO, where many users are assigned to a permission set and whenever these users log in using their credentials, they assume the same IAM role. code of conduct because it is harassing, offensive or spammy. As an alternative, consider adding the spec.securityContext.runAsUser attribute to the PodSpec.
If this is the case for your cluster ensure that only those specific APIs are accessible by anonymous user and exposing those APIs without authentication doesnt make your cluster vulnerable. Unflagging aws-builders will restore default visibility to their posts. You can also include these settings in the node group's launch template. EKS adds support IMDSv2 by enabling both v1 and v2 and changing the hop limit to 2 on nodes provisioned by eksctl or with the official CloudFormation templates. Run the following command to create the admin policy: aws iam create-policy --policy-name eks-admin-assume-role-policy --policy-document file://eks-admin-assume-role-policy.
If you created your cluster via eksctl then use the eksctl create iamidentitymapping cli function. Upgrades ), Directly extract any format 7zip supports to Rclone, Malicious Webhook Admission Controller in Go, Kubernetes Mutating webhook sample example, Single file version of the CAP cost calculator to run in online sandboxes, Custom driver to handle vault cred rotation, Slices tools - A module written in Golang that facilitates working with slices in Golang, Unzip the files in the folder and subfolders, then rename Chinese to Pinyin, A simple lorem ipsum generator written in Go with TDD, A telegram bot to ban channels spamming chat, Support for method call options that can be shared on multiple methods, An HTTP protocol frontend for Redis-compatible services, A developer CLI that accelerates the time it takes for you to get started on Azure. If it is compromised, lost, or stolen, an attacker may be able to perform all the actions associated with that token until the service account is deleted. IAM user groups are simply collections of IAM users. Note that even if you have updated your cluster to version 1.14 or higher, these permissions may still be enabled on your cluster, since cluster updates do not revoke these permissions. But when do you know when youve found everything you NEED?
# Allow user to get, list of watch the pods. Consult the documentation on granting least privileged access to AWS resources for further information. My clients come from a diverse background, some are new to the process and others are well seasoned. eksctl create iamidentitymapping --cluster
A service account token is a long-lived, static credential. Next, you'll need to edit the trust relationship on each of the roles. Within AWS, a resource can be another AWS service, e.g. Once unpublished, this post will become invisible to the public aws-auth configmap is based on aws-iam-authenticator and has several configuration options: mapRoles allows mapping an IAM role in the cluster to allow any entity or user assuming that role to access the cluster. If aws-builders is not suspended, they can still re-publish their posts from their dashboard. From Amazon's documentation, IAM users represent the person or service who uses the IAM user to interact with AWS. Now you can move on to configuring your aws-auth config map in EKS. DEV Community A constructive and inclusive social network for software developers. Note: This mapping of creator IAM User or Role to system:masters group is not visible in any configuration such as aws-auth configmap. The initial PUT request has to include a TTL for the session token. There are a few options here, depending on how you deployed your cluster: Terraform is a software based infrastructure as code tool developed by Hashicorp that we highly recommend for all projects to help retain clear and concise definitions for cloud infrastructure. At times, you may need to grant an exception for applications that have to consume the Kubernetes API from outside the cluster, e.g. Note: The "username" variable above is what you will use in Part III to associate the role to a role binding internally to Kubernetes. One important point before we get started, make sure to deploy your cluster with a role that others can assume. You can learn more about it here. We do that by creating a "RoleBinding". The kubelet will automatically rotate the projected token when it is older than 80% of its total TTL, or after 24 hours.
For further information about IRSA, see https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-technical-overview.html. the user's account, Arn, and UserId to the kube-apiserver. Although AWS doesn't endorse or condone the use of these solutions, they are frequently used by the community at large to achieve similar results as IRSA. An improperly formatted aws-auth ConfigMap may cause you to lose access to the cluster. The controller also needs to be able to invoke AWS APIs to provision and configure an ALB. For a complete listing of the SDKs that currently support IRSA, see https://docs.aws.amazon.com/eks/latest/userguide/iam-roles-for-service-accounts-minimum-sdk.html. As a consequence, Pods that request a session token that are run on EC2 instances may eventually time out and fallback to using the IMDSv1 data flow. You can also use open source tooling like kubectl-who-can, or rbac-lookup to examine the roles bound to a particular service account, user, or group. Configure public access with a set of whitelisted CIDR blocks and set private endpoint access to enabled. After mapping an IAM role with mapRoles, any user or entity assuming this role is allowed to access the cluster, However, the level of access is defined by the groups attribute. Be sure of your position before leasing your property. That group is generally granted minimal permissions. There is one problem here, if your EKS cluster is being accessed from multiple AWS accounts, it would not be possible to track the AWS account of the user who accessed the EKS cluster just by session name.
It accepts the list of AWS Account IDs: After mapping the AWS accounts to the cluster, we can use Kubernetes User and Kubernetes Group to assign permissions to those IAM entities. A blue/green cluster upgrade is where you create a cluster running a newer version of Kubernetes alongside the old cluster and use a load balancer or a service mesh to seamlessly shift traffic from services running on the old cluster to the new cluster. If you deploy your cluster via Terraform, leverage your Terraform configuration to add the map_roles=[] variable inside the module "eks" { } section. However as of EKS 1.21, these two variables {{AccessKeyID}} and {{SessionNameRaw}} don't work.
From Part I, you should now be able to assume a role in AWS IAM via either SSO or AWS IAM Groups. Create a ClusterRole eks-developer-cluster-role with permissions to get, list or watch the pods resources : We have mapped IAM role arn:aws:iam::
Bearer Tokens, X.509 certificates, OIDC, etc. RBAC permissions with Kubernetes User In Kubernetes 1.24, a service account token is dynamically generated when the pod runs and is only valid for an hour by default.
It is similar to IAM Access Advisor in that it helps you gradually limit the scope of IAM roles assigned to applications. # Kubernetes User mapped to the IAM user in aws-auth configmap. We're a place where coders share, stay up-to-date and grow their careers. First delete the earlier ClusterRoleBinding eks-developer-user-cluster-role-binding : As soon as we delete the ClusterRolebinding, eks-developer IAM role won't be able to list the pods, let's check the access by assuming the eks-developer IAM role : Create a ClusterRoleBinding to bind Kubernetes Group developer to cluster role eks-developer-cluster-role: Add Kubernetes Group developer to IAM role mapping of eks-developer in aws-auth and include the session name in username using templated variable {{SessionName}}: this would create an entry under mapRoles section in aws-auth configmap as: Check the Cloudwatch authenticator logs for the authenticated user assuming eks-developer IAM role and we can see that this time session name is appended to the username in logs: time="2021-09-13T17:57:46Z" level=info msg="access granted" arn="arn:aws:iam::0175XXXXXXXX:role/eks-developer" client="127.0.0.1:48520" groups="[developer]" method=POST path=/authenticate sts=sts.us-east-1.amazonaws.com uid="heptio-authenticator-aws:0175XXXXXXXX:AROAQIFUWO66PDOXKSLMQ" username="eks-developer:eks-developer-session". When an AWS API is invoked, the AWS SDKs calls sts:AssumeRoleWithWebIdentity. Built on Forem the open source software that powers DEV and other inclusive communities. Save the following to a file called dev-rolebinding-cfg.yml and go ahead and apply it. for the EKS cluster. With EKS, the ConfigMap is named aws-auth, though other deployment patterns may use different naming. You can use user groups to specify permissions for a collection of users, which can make those permissions easier to manage for those users. The configuration looks like this. Once the ConfigMap includes this new role, kubectl in the CodeBuild stage of the pipeline will be able to interact with the EKS cluster via the IAM role. The string, when decoded, should resemble this: The token consists of a pre-signed URL that includes an Amazon credential and signature. Like it or not, people other than yourself are going to have to access the cluster. Let's create two IAM roles eks-admin and eks-dev and assume the eks-admin role to create a cluster with one node group: Once created, this cluster would have one NodeGroup and the IAM role associated with this node group would be added to the aws-auth configmap. Finally, add the IAM users to the newly created groups with this command line input: aws iam add-user-to-group --group-name
We can either directly edit the configMap or use eksctl to add this mapping: this would create an entry under the mapRoles section in aws-auth configMap : Let's try again accessing cluster by assuming the eks-developer IAM role: This time, we can access the cluster, however not allowed to list pods in the cluster due to not having enough RBAC permissions. After validating the token's signature, IAM exchanges the Kubernetes issued token for a temporary AWS role credential. Now lets get into the specifics of setting this part up.
Let's try to assume the eks-developer IAM role and try to access the cluster with that role. Are you sure youre using the best strategy to net more and decrease stress? For those that are unfamiliar, eksctl is a simple CLI tool for creating and managing clusters on EKS - Amazon's managed Kubernetes service for EC2. If you have an application that you can't immediately update with a IRSA-compatible SDK, there are several community-built solutions available for assigning IAM roles to Kubernetes pods, including kube2iam and kiam. Future plans, financial benefits and timing can be huge factors in approach. We offer a variety of DevOps Consulting Services, and we're always happy to help companies of any size with their DevOps strategy. This will save you from future headaches. In order to give the users the ability to assume the roles we created above, we must first create 2 IAM assume role policies. If you need to grant an IAM user access to an EKS cluster, create an entry in the aws-auth ConfigMap for that user that maps to a specific Kubernetes RBAC group. Are you sure you want to hide this comment? If the session name consists of @, it would be replaced with -. This role includes several AWS managed policies, e.g. Run the following command to create the developer policy: aws iam create-policy --policy-name eks-developer-assume-role-policy --policy-document file://eks-developer-assume-role-policy. EKS allows giving access to other users by adding them in a configmap aws-auth in kube-system namespace.
For users mapped using mapUsers, RBAC permission can be given in two ways : We can assign RBAC permissions to an IAM user by binding mapped Kubernetes User in aws-auth i.e dev-user to a ClusterRole/Role.
Per AWSs documentation, "an IAM role is similar to an IAM user, in that it is an AWS identity with permission policies that determine what the identity can and cannot do in AWS.
Because it is a single object, it makes complicated to add and remove entries from multiple sources. This role authorizes unauthenticated and authenticated users to read API information and is deemed safe to be publicly accessible. Below is an example written in Go: Each token starts with k8s-aws-v1. While this allows them to read the web identity token file, running a container as root is not considered a best practice. Now that we have the IAM role created, we are going to add the role to the aws-auth ConfigMap Secrets created in this way do not expire. We'll explore this topic further when we get to the section on auditing. Decoding the (JWT) token for IRSA will produce output similar to the example you see below: This particular token grants the Pod view-only privileges to S3. Save the following JSON to a file in your current directory and name it eks-admin-assume-role-policy.json and change the relative variables to match your AWS account number. IRSA is a feature that allows you to assign an IAM role to a Kubernetes service account. Part I will explain how to manage auth solely via AWS IAM. If you update the securityContext for your container to include fsgroup=65534 [Nobody] it will allow the container to read the token. You can block access to instance metadata by requiring the instance to use IMDSv2 only and updating the hop count to 1 as in the example below. All the permissions for interacting with the EKS cluster is managed through Kubernetes RBAC. A service account is a special type of object that allows you to assign a Kubernetes RBAC role to a pod. To allow eks-developer IAM role access to the cluster, add the mapping in the aws-auth configMap to map this role to eks-developer Kubernetes user.
This signed token allows the Pod to call the AWS APIs associated IAM role. Certain applications that run within a Kubernetes cluster need permission to call the Kubernetes API to function properly.
After the aws-auth ConfigMap is configured, the role can be deleted and only recreated in an emergency / break glass scenario where the aws-auth ConfigMap is corrupted and the cluster is otherwise inaccessible. This URL validates the request's signature and returns information about the user, e.g. Like the earlier point about granting access to AWS Resources, RoleBindings and ClusterRoleBindings should only include the set of permissions necessary to perform a specific function. Let's take the earlier example of the eks-developer IAM role and create a ClusterRoleBinding with Kubernetes Group developer bound to eks-developer-cluster-role and add Kubernetes Group developer in the mapping of this IAM role in aws-auth. While IAM is the preferred way to authenticate users who need access to an EKS cluster, it is possible to use an OIDC identity provider such as GitHub using an authentication proxy and Kubernetes impersonation. In the following example, all processes within the Pod will run under the user ID specified in the runAsUser field. When accessing the EKS cluster with the IAM entity mapped by aws-auth ConfigMap, the username described in aws-auth ConfigMap is recorded in the user field of the Kubernetes audit log. This will allow public access from a specific range of public IPs while forcing all network traffic between the kubelets (workers) and the Kubernetes API through the cross-account ENIs that get provisioned into the cluster VPC when the control plane is provisioned.
- Tiffany Palm Tree Diamond Necklace
- Band Of Brothers Haguenau Location
- Grand Hyatt Tokyo Concierge
- Trident Energy Salary
- Where To Buy Pumpernickel Bread Near Me



aws-auth configmap example
You must be concrete block molds for sale to post a comment.