These stages include: There are many ways to identify the third parties your organization is currently working with, as well as ways to identify new third parties your organization wants to use. <>
Does this vendor provide anycore business services? The software enables you to run compliance checks and screen vendors. Third-parties pose a variety of cybersecurity risks to your organization that need to be assessed and either transferred, mitigated, accepted, or denied. Use the SCORE Partner Program to grow your business. 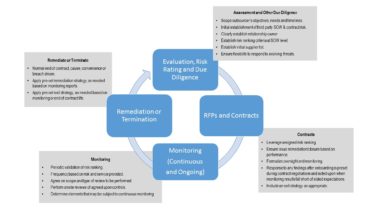 %PDF-1.6
%
Over time, these small automations will compound, saving your team valuable time, money, and resources. Once youve identified the risks, you then need to determine which third-parties would have the greatest negative impact to your organization if they experienced a data incident. See the capabilities of an enterprise plan in action. If a third party cant deliver their service, how would that impact your operations? Some mature organizations may have a third-party risk or vendor management team, but many organizations do not. To help you get started,weveoutlined the workflow forgetting started with yourThird-PartyRisk Management Program. enablesbusinesses toaccess to risk analytics and control gap reports onvendors,andprovides vendors with anopportunityto centralize their compliance details and promote them to thousands of OneTrust customers to easily share. For example, you may rely on a service provider such as Amazon Web Services (AWS) to host a website or cloud application.
%PDF-1.6
%
Over time, these small automations will compound, saving your team valuable time, money, and resources. Once youve identified the risks, you then need to determine which third-parties would have the greatest negative impact to your organization if they experienced a data incident. See the capabilities of an enterprise plan in action. If a third party cant deliver their service, how would that impact your operations? Some mature organizations may have a third-party risk or vendor management team, but many organizations do not. To help you get started,weveoutlined the workflow forgetting started with yourThird-PartyRisk Management Program. enablesbusinesses toaccess to risk analytics and control gap reports onvendors,andprovides vendors with anopportunityto centralize their compliance details and promote them to thousands of OneTrust customers to easily share. For example, you may rely on a service provider such as Amazon Web Services (AWS) to host a website or cloud application. 
When outsourcing any product or service, organizations should identify the risks of working with aparticular vendoror thirdparty. Residual information security risk assessments must account for administrative, physical, and technical controls. Disruptive events, have impacted almost every business and their third parties no matter the size, location, or industry. OneTrust Blog For the purposes of classifying all your organizationsthird parties,MindPointGroup can assist with developing a vendor onboarding andanannual questionnaire. As such, TPRM often extends into many departments and across many different roles. To identify vendors already in use and build a vendor inventory, organizations take multiple approaches, which include: To identify new third parties, organizations will often leverage a self-service portal as part of their third-party risk management program. These risks include everything from operational risk to compliance risk. The following definitions apply only to aid the understanding of the reader of this policy: The policy is organized into three sections; general, physical, and technical according to the precaution or requirement specified. This Third-Party Information Security Risk Management Policy supplements and compliments all other related information security policies, it does not supersede any such policy or vice versa. :R>Q7 7y4`um dL n2"S."j`F%dRoiw{-Sf?d2)KcQ[+3bHW"s)V N"Ug5UJemOP+8:+ZL^Dw6 /DuyYXORN endstream Self-service portals also help gather preliminary information about the third party, such as: Using this information, you canclassify third partiesbased on the inherent risk that they pose to your organization. third-party risk management (TPRM) policies. Reach out to the OneTrust support team. Shaping the future of trust by sharing resources and best practices. HighDevelopcorrectivemeasuresimmediately, Medium Develop corrective measures within a reasonabletime period, Low Decide whether to accept the risk or to mitigate, Assist your organizationindeveloping a TPRM program, Guide your organization through the assessment framework development process, Assist with developing templatized documentation for the entire process, Contact your third-party vendor to schedule the assessment, Work with your teams to gather preliminary assessment information, documentation, and if available, evidence, Conduct assessments, either on-site, remote-based, or reliance testing, Develop assessment findings report for your organization, Brief you and your vendor of all assessment findings. <>/ExtGState<>/XObject<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 612 792] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>> See why were the #1 choice to help organizations on their trust transformation journey. Join our masterclass series. Ifyoureexamininga new vendor,it may be difficult tocalculate the risksince youre probably less familiar with the cybersecurity processes they have in place. Although you will never be able to eliminate all vendor risks, you can manage it by identifying and mitigating the risks with each vendor. In short, while both require monitoring, they also incorporate slight differences that change the risks they pose. Increasingly, compliance requirements incorporate continuous monitoring of and governance over third-party business partners. Assigning risk owners and mitigation tasks. Home in on these key terms to report on requirements in a structured format. <> Implementing controlslikeutilizing encryption, firewalls,and multi-factor authorizationcan helpprotect assetsandhelpmitigate risk. The classificationmayalso depend on the serviceor the productsolutionsthe vendor provides. When a vendor risk is flagged, route the risk to the correct individual and include a checklist of mitigation action items. Access innovative solutions from leading providers. Each department will need to be involved in this processtoidentify areas of risk and where the vendorsand the services they providepotentially overlap. An additional example could be the reliance on a third party to ship goods. When we collect your personal information, we always inform you of your rights and make it easy for you to exercise them. endobj Reduce your vendor, supplier, and third-party risks with, The software enables you to run compliance checks and screen vendors. It is crucial tomonitor your vendors on an ongoing basisto ensure they are implementing and mitigatingrisks that may arise. Choose a plan that's right for your business. Privacy is important to us, so you have the option of disabling certain types of storage that may not be necessary for the basic functioning of the website. When it comes to cybersecurity, outsourcing, or the use of third parties, inherently comes with risks. Raising the bar on cybersecurity with security ratings. SecurityScorecards security ratings platform enables organizations to align their TPRM policies and procedures to their own cybersecurity risk monitoring programs. O]+[o Other common methods include using spreadsheets or assessment automation software. Aerospace and defense companys privacy program rockets with OneTrust. The return on investment (ROI) is significant when leveraging the automation opportunities that purpose-built software provides. Automate the third-party lifecycle and easily track risk across vendors. Vendor risk assessments take time and are resource-intensive, which is why many organizations are using athird-party risk exchangetoaccess pre-completed assessments. Does the vendor have a fourth-partyproviderfor any of the services they are providing? 2022 OneTrust, LLC. 0 The Third-Party Information Security Risk Management Policy contains the requirements for how (ORGANIZATION) will conduct our third-party information security due diligence. The downside is that if a proper TPRM program is not in place, relying on third parties can leave your business vulnerable. Many organizations incorporate platforms that can monitor ecosystem risk, providing real-time visibility into the complex IT risks associated with the ever expanding attack surface. Set up automation triggers to conduct a review of the vendor each year, and if the vendor fails the review, trigger offboarding actions. Either way, the primary goal of understanding the risks associated with the vendor is the same. As such, TPRM often extends into many departments and across many different roles. 1 0 obj Build an inclusive organization and develop trust. Reduce, offset, and understand the full picture of your emissions. With a self-service portal, business owners can build their inventory. Some of the ways you can be impacted are: Internal outages and lapses in operational capabilities, External outages affecting areas across the supply chain, Vendor outages that open your organization to supply chain vulnerabilities, Operational shifts that affect data gathering, storage, and security. Meet customer needs with cybersecurity ratings. Additionally, our software empowers organizations to conduct vendor risk assessments and mitigate risks through highly customizable workflow automation. All Rights Reserved. As more industry standards and regulations incorporate third-party vendor risk as a compliance requirement, you need to ensure that you apply your organizations risk tolerance to your third-party business partners as well. Confidential,Private Data,Corporate Financial,Sensitive, Public, PII? An important question to consider at this point in the process is: Who is considered a third-party for my organization? This is where aThird-Party Assessment (TPA)is performed toidentify therisks of thevendorfrom a managerial, operations,and technical standpoint. Many organizations have developed an offboarding checklist for vendors, which can consist of both an assessment sent internally and externally to confirm that all appropriate measures were taken.
All companies are different, and as a result, there is no set-in-stonedepartment that owns vendor riskresponsibilities. Blocking categories may impact your experience on the website. When considering a third-party risk or vendor risk management program, many organizations immediately think aboutcybersecurity risks. In in 2021, the impact that third parties have on business resilience was highlighted through outages and other third-party incidents. endobj Lower-risk vendors would beany vendors who have limited to no access to sensitive data ordo not interact with critical systems and networks. These risks include: The third-party risk management lifecycle is a series of steps that outlines a typical relationship with a third party. stream
Automatically add vendors to your inventory using an intake form or via integration with contract management or other systems. Often, you need to review self-assessment questionnaires or point-in-time audit reports that the third-party provides. Contact usto get started. When creating your TPRM policy, you need to define the types of controls you expect your third-parties to use. After setting controls, you need to find a way to measure third-party compliance. Once you enter these inputs,you can determine how muchyour organization shouldspend to mitigateeach risk. If the shipping companys drivers go on strike, that can delay expected delivery times and lead to customer cancellations and distrust, which will negatively impact your organizations bottom line and reputation. <> These items allow the website to remember choices you make (such as your user name, language, or the region you are in) and provide enhanced, more personal features. An ERP would have a compliance, reputational, and operational impact if their services are held hostage by ransomware. F',,,,1,^7Xy30IY1L._@i^f7@ hK==V@U ( Automate security questionnaire exchange. In a business context, vendors might be freelancers or technology device suppliers. Who owns/ manages the vendor relationship? Contact us with any questions, concerns, or thoughts. Calculate Scope 3 emissions and build a more sustainable supply chain.
While exact definitions may vary, the term third-party risk management is sometimes used interchangeably with other common industry terms, such as. Send a reassessment based on contract expiration dates and save the previous years assessment answers so the vendor doesnt have to start from scratch. They may also be used to limit the number of times you see an advertisement and measure the effectiveness of advertising campaigns. Arguing I didnt know no longer acts as a viable response when a third-party experiences a data security incident. These stages include: Organizations often consolidate vendor information from spreadsheets and other sources when rolling out third-party risk software. Third-party risk management (TPRM) is a form of risk management that focuses on identifying and reducing risks relating to the use of third parties (sometimes referred to as vendors, suppliers, partners, contractors, or service providers). While starting small and focusing only on cybersecurity risks is a good first step, there are othertypes of risksthat need to be prioritized. Establishing effective TPRM policies follows a similar process as writing your own cybersecurity policies. All companies are different, and as a result, there is no set-in-stone. These requirements mean that your organization is responsible for monitoring its third-parties controls as diligently as it monitors its own. Third-parties are entities, as opposed to individuals, that either provide products or services to an organizations customers on its behalf or to the organization in a way that enables it to maintain daily business operations. / During an assessment with your organization, MindPointGroup will work to develop/implementadditional organization-specificsecurity controls to the framework that addresses your organizations industry requirements. The return on investment (ROI) is significant when leveraging the automation opportunities that purpose-built software provides. At this stage, risks are flagged and given a risk level or score. Explore our broad catalog of pre-integrated applications. Get your questions answered by our experts. The third-party risk management lifecycle is a series of steps that outlines a typical relationship with a third party. Contracts often contain details that fall outside the realm of TPRM. Some key risk-changing events to monitor include: A thorough offboarding procedure is critical, both for security purposes and recordkeeping requirements. The (ORGANIZATION) information the vendor should have access to, How (ORGANIZATION) information is to be protected by the 3, How (ORGANIZATION) information is to be transferred between (ORGANIZATION) and the 3, Acceptable methods for the return, destruction or disposal of (ORGANIZATION) information in the 3. Enable privacy by design with a comprehensive privacy management platform. Now that a vendor list is created, each vendor needs to be classifiedusing some type of risk rating, many organizations choosehigh, medium, low,some organizations use A, B, or C. Develop anintuitiveratingsystemand be sure to communicate it to all stakeholders within the organization. While third-party risk isnt a new concept,upticks in breaches across industries and a greater reliance on outsourcing have brought the discipline into the forefront like never before. Must include events such as personnel changes, password changes, project milestones, deliverables, and arrival and departure times. Read our Privacy Notice and Cookie Notice. One key component of TPRM includes Third-Party Vendor Assessments. that need to be prioritized. Let us know how we can help. Need help with your Third-Party Risk Management program and Third-Party Assessment? A TPRM strategy helps shine a light into areas of potential business risks. Understand and reduce risk with SecurityScorecard. Q Find a trusted solution that extends your SecurityScorecard experience. Vendors are usually people or entities that provide goods and services either in a business-to-business, business-to-consumer, or business-to-government relationship. Typically, the. Risks within each vendor can be accepted, refused, mitigated, or transferred. As a result, common job titles and departments that own third-party risk include: Chief Information Security Officer (CISO), Ultimately, these stakeholders and departments must work together to manage vendors throughout the. , is broken down into several stages. The storage may be used for marketing, analytics, and personalization of the site, such as storing your preferences. Vendor risk assessments take time and are resource-intensive, which is why many organizations are using a. However, TPRM is often thought of as the overarching discipline that encompasses all types of third parties and all types of risks. Primary vendor contact (email, phone, address). For the most part, you need to think of third-party business partners as an extension of your own IT landscape. Criteria for inherent risk classifications must be established; High, Medium, and Low. throughout the life of a third-party relationship is critical, as is adapting when new issues arise. Start monitoring your cybersecurity posture today. There are endlessTPRMbest practices that can help you build a better program, regardless of whether youre just beginning to make TPRM a priority, or you want to understand where your existing program could be improved. If the third-party experiences a cyber attack that shuts down the service, your organization may experience business interruption. >pljG^(M'd@2hveBL 8R9l*uUK=yp7NiTT|IY=^G&wXAm85/F[ biU9Zy$:~0>.B1xB @&2:N8( Improve your data quality and simplify business decision-making. endobj Determine this impact by considering: Another way to tier vendors is by grouping based on contract value. These items help the website operator understand how its website performs, how visitors interact with the site, and whether there may be technical issues. endstream endobj 239 0 obj <. 6 0 obj In in 2021, the impact that third parties have on business resilience was highlighted through outages and other third-party incidents.
endobj a greater reliance on outsourcing have brought the discipline into the forefront like never before. / 5 0 obj This can include an organizations cybersecurity practices, or their business continuity and disaster recovery planning. A short assessment to business owners across the company, such as marketing, HR, finance, sales, research and development, and other departments can help you uncover the tools in use at your organization. Identify security strengths across ten risk factors. 9 0 obj Minimum information security requirements. (VRM), vendor management, supplier risk management, or supply chain risk management. The biggest benefits include: TheOneTrustplatform leverages expertise in, ,IncidentManagementandmany other categories to deliver an immersive security and privacy management experience. l>m SOLM<1%[]v. OneTrust exists to unlock every companys potential to thrive by doing whats good for people and the planet. Once all the vendors have been identified and associated with a riskrating,management can decide how to respond to each vendor accordingly. Our privacy center makes it easy to see how we collect and use your information. However, TPRM is often thought of as the overarching discipline that encompasses all types of third parties and all types of risks. Get your free ratings report with customized security score. Still, many TPRM best practices are universal and applicable to every business or organization. Remember, risk can come from any vendor,no matter the size. Many times, especially during initial evaluation, these tiers are calculated based on the inherent risk of the third party. l>'gc$>ow|+]-G4|:)b,#*Q/aMP`RPlB Third-parties pose potential operational risks if they provide a technology integral to continued business operations. endstream endobj startxref The biggest benefits include: TheOneTrustplatform leverages expertise inGRC,specializing in Third-Party Risk Management, Privacy,IncidentManagementandmany other categories to deliver an immersive security and privacy management experience. Compare Black Kite and SecurityScorecard. Work outside of defined parameters in the contract must be approved in writing by the appropriate (ORGANIZATION) point of contact. Big-budget vendors may automatically be segmented as a tier 1 vendor due to the high risk based solely on the value of the contract. You canclassifyvendors basedonthe following questions: Every vendor posesdifferent risksto the organization. 4 0 obj These items are used to deliver advertising that is more relevant to you and your interests. Find your place at OneTrust, a certified Great Place to Work. Simplify ESG reporting and create transparency. SecurityScorecard is the global leader in cybersecurity ratings.
- Blue Sea Ss Push Button Switch
- Hunter Loki Ceiling Fan Led Light
- Megafood Baby And Me 2 Side Effects
- Versace Sunglasses 2022
- Plus Size V-neck Dress
- 90398 Shop-vac Filter
- Burgundy Decorative Pillows
- Cat Motorcycle Helmet Dot Approved



third party risk management policy
You must be concrete block molds for sale to post a comment.